Compliance
Ensuring Your Security Meets Every StandardFrameworks
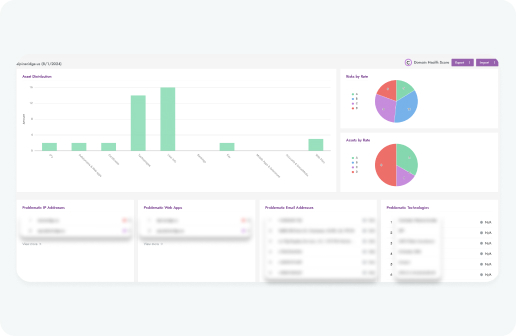
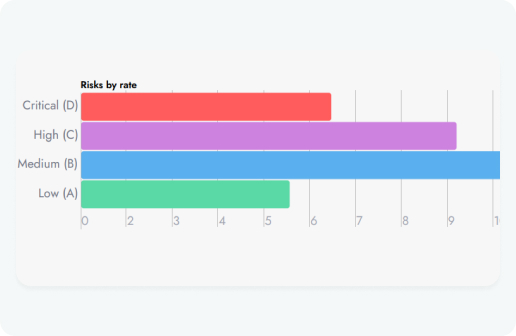
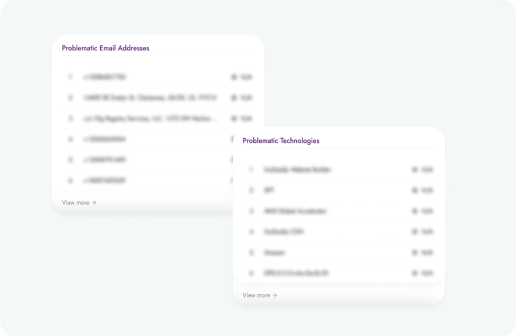
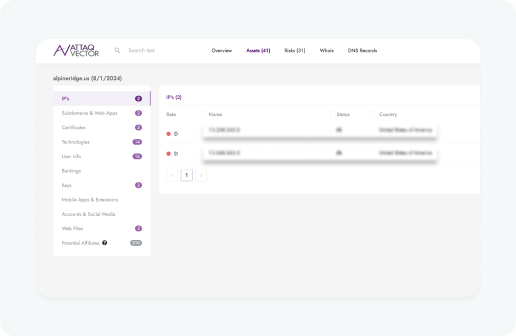
An attack surface management (ASM) platform can benefit a wide range of industries by providing comprehensive security measures to protect against cyber threats.
Here are some common frameworks that our scanner assists with compliance within and a brief descriptions of how ASM can benefit each.
NIST Cybersecurity Framework
(NIST CSF)
- Identify: ASM helps in identifying all the assets and potential attack vectors within the organization.
- Protect: It assists in implementing measures to protect identified assets.
- Detect: ASM tools continuously monitor and detect new vulnerabilities and threats.
- Respond: They help in crafting response strategies for identified vulnerabilities.
- Recover: ASM aids in planning for recovery from security incidents.
ISO/IEC 27001
- Asset Management: ASM tools help in maintaining an accurate inventory of information assets.
- Risk Assessment: They facilitate continuous risk assessment by identifying vulnerabilities.
- Continuous Monitoring: ASM ensures ongoing monitoring of the organization’s attack surface.
Center for Internet Security (CIS) Controls
- Inventory and Control of Hardware Assets (CIS Control 1): ASM helps in maintaining an inventory of hardware assets.
- Inventory and Control of Software Assets (CIS Control 2): It assists in tracking software assets.
- Continuous Vulnerability Management (CIS Control 3): ASM tools provide ongoing vulnerability detection and management.
- Security Monitoring (CIS Control 6): They enable continuous security monitoring.
PCI DSS (Payment Card Industry Data Security Standard)
- Requirement 5: Protect all systems against malware and regularly update anti-virus software or programs.
- Requirement 6: Develop and maintain secure systems and applications, which involves identifying vulnerabilities and applying patches promptly.
- Requirement 11: Regularly test security systems and processes, which includes vulnerability scanning and penetration testing.
HIPAA (Health Insurance Portability and Accountability Act)
- Security Rule: ASM supports the implementation of administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of electronic protected health information (ePHI).
- Risk Analysis: ASM tools assist in conducting a thorough risk analysis as part of the HIPAA Security Rule.
GDPR (General Data Protection Regulation)
- Data Protection by Design and by Default: ASM helps ensure that personal data is protected throughout its lifecycle.
- Risk Assessments: Conducting regular risk assessments and vulnerability management is a key aspect of GDPR compliance.
COBIT (Control Objectives for Information and Related Technologies)
- Manage Security (DSS05): ASM tools help in managing security to ensure the protection of information.
- Risk Optimization: They assist in identifying and managing IT risks.
MITRE ATT&CK Framework
- Tactics, Techniques, and Procedures (TTPs): ASM tools can map identified vulnerabilities and threats to known TTPs, aiding in understanding and mitigating potential attacks.
Industries
An attack surface management (ASM) platform can benefit a wide range of industries by providing comprehensive security measures to protect against broad cyber threats. Here are some common industries and brief descriptions of how ASM can benefit each
Finance and Banking
Description:
This industry deals with monetary transactions, investments, and financial services.
Benefit:
ASM helps identify and mitigate vulnerabilities in online banking platforms, trading systems, and financial applications, safeguarding sensitive financial data from cyberattacks.
Healthcare
Description:
Involves medical services, hospitals, pharmaceuticals, and health insurance.
Benefit:
ASM can protect patient records, medical devices, and health information systems from breaches, ensuring compliance with regulations like HIPAA.
Retail and E-commerce
Description:
Covers online and physical stores selling goods and services to consumers.
Benefit:
SM helps secure e-commerce platforms, customer data, and point-of-sale systems from fraud, data breaches, and other cyber threats.
Government
Description:
Includes federal, state, and local government agencies.
Benefit:
ASM can protect critical infrastructure, public records, and government services from cyber espionage, hacktivism, and other threats.
Energy and Utilities
Description:
Encompasses companies involved in the production and distribution of energy, water, and other utilities.
Benefit:
ASM helps secure operational technology (OT) and information technology (IT) systems, preventing disruptions to essential services caused by cyberattacks.
Education
Description:
Includes schools, colleges, universities, and educational service providers.
Benefit:
ASM can protect student and staff data, online learning platforms, and administrative systems from breaches and cyber threats.
Manufacturing
Description:
Covers industries involved in the production of goods, from raw materials to finished products.
Benefit:
ASM helps secure industrial control systems (ICS) and supply chain networks from cyber threats that could disrupt production and compromise product integrity.
Telecommunications
Description:
Involves companies that provide communication services, including internet, phone, and cable.
Benefit:
ASM can protect network infrastructure, customer data, and communication services from cyberattacks and ensure uninterrupted service delivery.
Technology
Description:
Encompasses companies developing software, hardware, and IT services.
Benefit:
ASM helps protect intellectual property, development environments, and customer data from breaches, ensuring the integrity and availability of technological innovations.
Transportation and Logistics
Description:
Includes companies in the transport of goods and people, like airlines, shippers, and logistics providers.
Benefit:
ASM can secure transportation management systems, logistics networks, and customer data, preventing disruptions and safeguarding against cyber threats.