Empowering Your Cybersecurity
Journey with Comprehensive Services
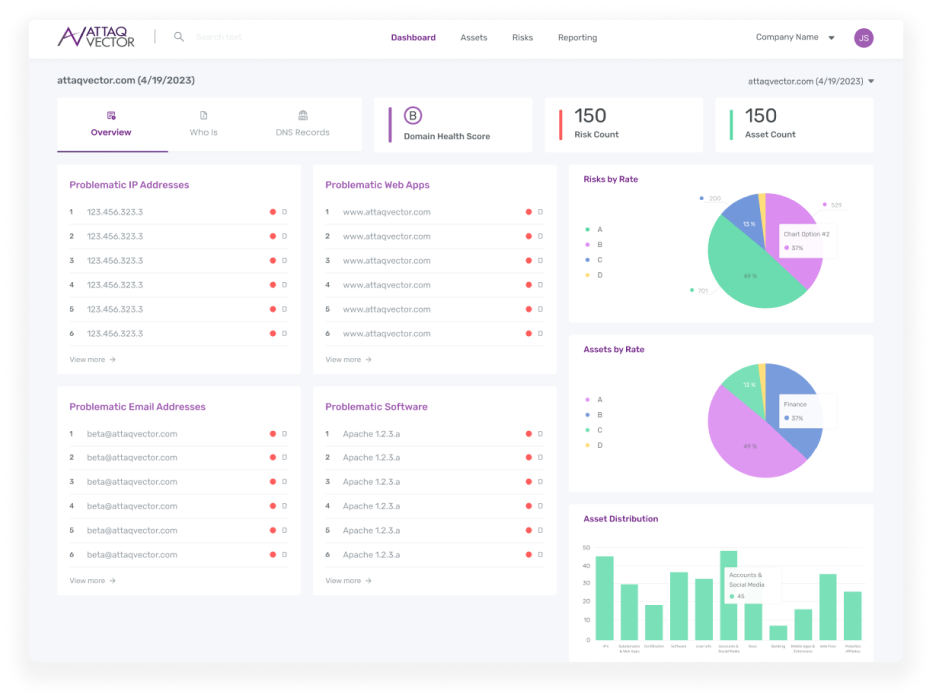
Discovery
Discovery scan which is initiated via the verification Enumerating Network Assets: Identifying and cataloging all devices, servers, and endpoints the clients digital fooprint, including IP addresses, domain names, and open ports. This helps in understanding the client’s scope.
Firewall Scanning
Firewall scan which is Getting the IP address and mapping what ports are open and closed. Starting with port scans to identify open ports on the firewall. This helps them determine which services are exposed to the internet. Open ports could be potential attack vectors, so testers may probe these ports further to identify vulnerabilities. Once this phase is done we move to Protocol Analysis and so on.

Website Scanning
Website scanning if the client has a web app server behind the firewall it will do web app scans, AJAX spider scans, and more to find points of interest to leak data.

Technology Scanning
Technology scanning meaning what is it made with? What language, or Tech stack is used to get this Web App off the ground. Also this will include miscellaneous scans to identify other various versioning and programs included in the clients digital footprint.

Server Scanning
Server scanning,Fingerprinting what version and OS that server is running. What Programs and map them to that specific port and what fingerprint those versions and any other information related to that specific server(s)

Application Scanning
Application scanning involves examining software applications for security vulnerabilities, crucial for identifying and mitigating risks exploited by attackers. It’s an essential part of security strategy, enabling proactive detection of vulnerabilities to prevent security breaches and data compromises. Leveraging ASM platforms like Attaq Vector involves resolving application version numbers and comparing them to known vulnerabilities in databases like MITRE.org’s CVEs.

Vulnerability Scanning
External vulnerability scanning involves systematically examining an organization’s internet-facing systems to detect potential security weaknesses, aiming to prevent exploitation by external attackers. Automated scanning tools are commonly used to identify known vulnerabilities and misconfigurations, with regular scanning being crucial to keep up with evolving threats and comply with industry standards. The results are documented in reports, aiding in prioritizing and remedying critical issues, although it’s emphasized that this is just one part of a broader cybersecurity strategy which should include internal scanning, penetration testing, and continuous monitoring.

Penetration Testing
Penetration testing is just scratching the service on what exploits can be launched to penetrate that specific network and or device on the clients digital footprint.

Resolutions
Resolutions are proposed to most of the potential vulnerabilities found in the above categories by the platform. Through regularly-scheduled monitoring and analysis of the attack surface, the platform swiftly identifies and recommends remediation actions, streamlining the process for security teams and enabling them to efficiently address threats before they can be exploited. Additionally, integration with existing security tools and workflows ensures seamless remediation and enhances overall cybersecurity posture.
