Think Like an Attacker to Safeguard Your Company
Explore Your Complete
Attack Surface
Attaq Vector goes beyond the surface to help you uncover the complete landscape of potential threats facing your organization. With our platform, you gain a comprehensive view of your attack surface, shedding light on all potential vulnerabilities and entry points. This depth of insight is invaluable for proactive security measures. By understanding your digital environment from every angle, you can make informed decisions to fortify your defenses and keep your organization one step ahead of cyber threats.
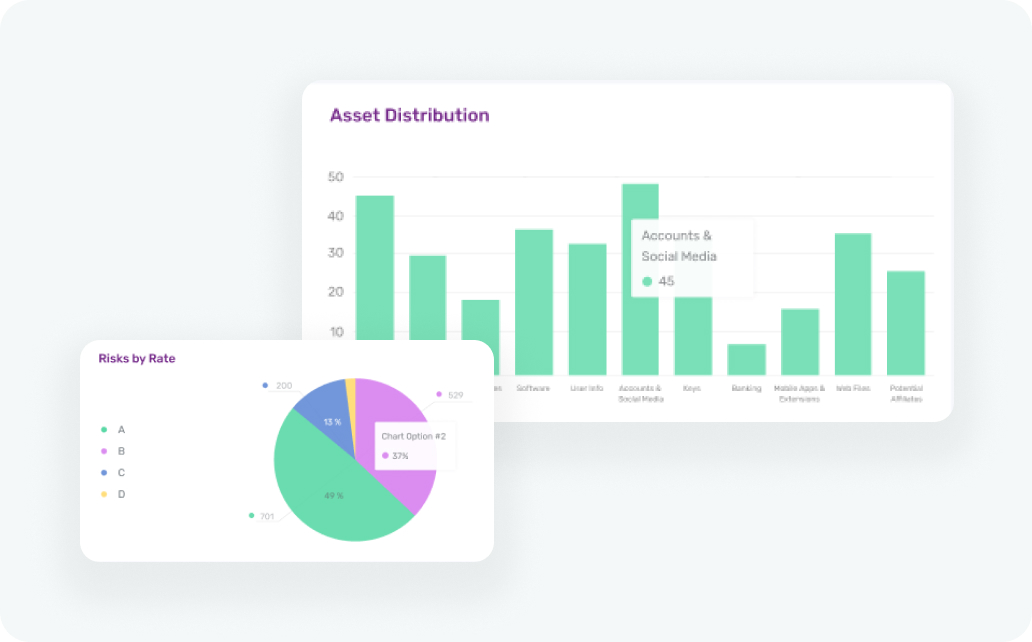
Real-time Scanning
Attaq Vector provides real-time scanning of your digital presence. Our automated system tirelessly monitors your attack surface, ensuring you’re always up to date with emerging threats. This proactive approach allows you to detect vulnerabilities as soon as they surface, giving you a significant advantage in staying secure. With the ability to respond swiftly to evolving security challenges, you can safeguard your organization’s valuable assets and maintain trust with your customers.
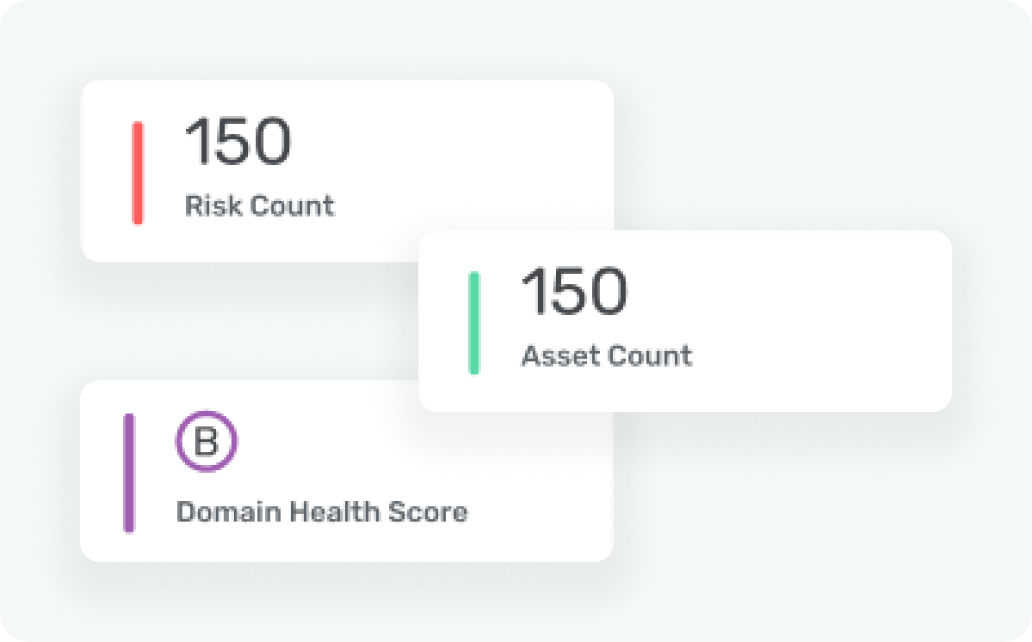
Actionable Intelligence
Beyond mere identification, Attaq Vector delivers actionable insights. Our platform empowers you to not only detect vulnerabilities but also prioritize and address them effectively. With a clear understanding of the risks your organization faces, you can focus your efforts and resources where they matter most. This strategic approach to cybersecurity enables you to enhance your security posture, reduce potential threats, and protect your valuable data.
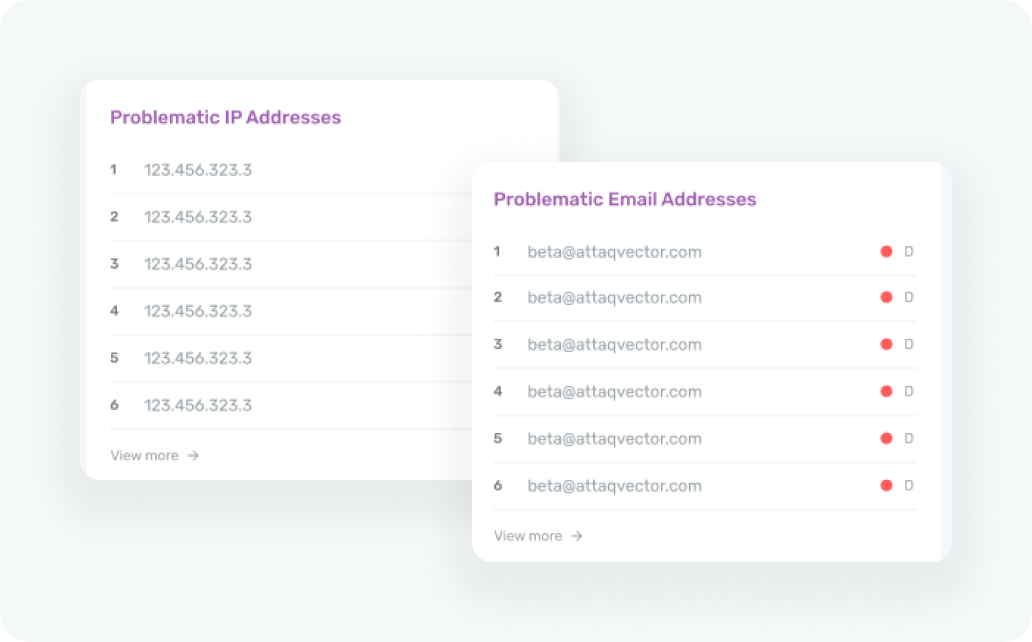
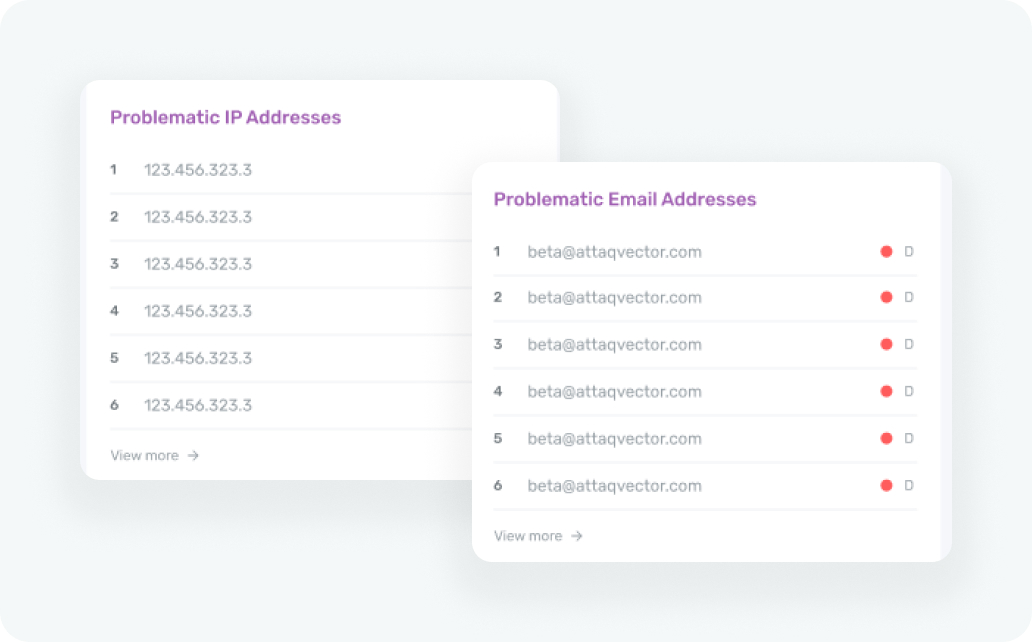
In-Depth Risk Assessment
Attaq Vector provides in-depth risk assessment reports. These reports offer a comprehensive understanding of your organization’s risk profile, covering vulnerabilities, their potential impact, and recommendations for mitigating them. Armed with this knowledge, you can make informed decisions regarding your security strategy, ensuring your resources are allocated where they are most needed. It’s a strategic advantage that helps you prioritize and address risks efficiently and reduce your organization’s exposure.
Our Approach
At Attaq Vector, our approach to cybersecurity is structured, user-focused, and designed to empower you. From defining your attack surface to providing actionable insights, our method ensures you’re in control of your cybersecurity strategy. Discover how our comprehensive approach can keep your digital assets secure.
The first step in using Attaq Vector is defining your organization’s attack surface. This involves specifying the digital assets, applications, and infrastructure you want to monitor. The platform will tailor its scanning to focus on these defined areas, ensuring that you’re looking at the right components from the start.
Firewall scanning refers to the process of examining and evaluating the configuration and effectiveness of firewalls deployed within an organization’s network.
Website scanning refers to the process of systematically examining and evaluating the security posture of a website or web application. The goal of website scanning is to identify potential vulnerabilities, weaknesses, or misconfigurations that could be exploited by attackers to compromise the confidentiality, integrity, or availability of the web assets.
Technology scanning refers to the ongoing process of monitoring, evaluating, and analyzing emerging technologies of the target domain. The goal is to stay abreast of new developments, threats, and solutions to adapt security strategies accordingly. Technology scanning is a proactive approach to understanding the evolving nature of cyber threats and the tools available to defend against them.
Server scanning refers to the process of systematically examining and assessing the security configuration, vulnerabilities, and overall health of servers of an organization’s external IT infrastructure. This activity is crucial for identifying potential weaknesses that could be exploited by malicious actors to compromise the confidentiality, integrity, or availability of the servers and the data they host.
Application scanning is the process of scrutinizing software applications to uncover security vulnerabilities, which is vital for pinpointing and addressing risks that attackers may exploit. This practice is integral to a robust security strategy as it allows for early detection of vulnerabilities, helping to thwart security breaches and safeguard against data compromises. Utilizing Application Security Management (ASM) platforms such as Attaq Vector entails the resolution of application version numbers and their comparison with known vulnerabilities stored in databases like MITRE.org’s CVEs.
External vulnerability scanning is the methodical inspection of an organization’s internet-facing systems to uncover potential security flaws, with the goal of thwarting external attacks. This process typically employs automated scanning tools to pinpoint known vulnerabilities and misconfigurations, underscoring the importance of regular scans to adapt to evolving threats and adhere to industry regulations. The findings are recorded in reports to help prioritize and address critical issues. However, it’s essential to recognize that external vulnerability scanning is just one component of a comprehensive cybersecurity strategy, which should also encompass internal scanning, penetration testing, and ongoing monitoring.
Penetration testing, often abbreviated as “pen testing,” is a proactive cybersecurity approach aimed at evaluating the security of computer systems, networks, or applications. It involves authorized simulated attacks on a system to identify vulnerabilities that malicious hackers could exploit. The goal is to assess the security posture of the target system, uncover weaknesses, and provide recommendations for strengthening defenses.
Our platform serves as a vital tool in identifying and mitigating vulnerabilities across an organization’s digital footprint. Leveraging its comprehensive scanning capabilities, the platform meticulously maps out potential weak points in systems, networks, and applications. Beyond detection, its value truly shines through in the proactive guidance it offers for remediation. By analyzing the discovered vulnerabilities in depth, the platform can provide tailored recommendations and actionable insights to address each identified risk. These suggestions may range from simple configuration changes and patch updates to more intricate security measures, all geared towards bolstering the organization’s defense against potential cyber threats. Through continuous monitoring and iterative feedback, the platform empowers security teams to not only identify vulnerabilities but also effectively prioritize and resolve them, thereby fortifying the organization’s overall cybersecurity posture.
Ongoing attack surface monitoring is indispensable for any business in today’s digital landscape due to the ever-evolving nature of cybersecurity threats. By frequently monitoring their attack surface, businesses can stay one step ahead of potential threats and vulnerabilities. This proactive approach enables organizations to identify and assess potential risks to their systems, networks, and data in real-time, allowing for timely mitigation measures to be implemented. Furthermore, ongoing monitoring provides valuable insights into emerging attack vectors and trends, empowering businesses to adapt their security strategies accordingly. Ultimately, investing in recurrent attack surface monitoring not only enhances the overall security posture of a business but also helps safeguard its reputation, customer trust, and financial wellbeing.
Security & Vulnerability Checks
Broad checks for IP, URL or subnet reputation (more than 100 checks including malware, phishing, ransomware, denial-of-service attacks, man-in-the-middle attacks, spam, scanner, etc
Certificate checks: (expiration, low key size, self-signed, algorithm strength
CVE detection (stands for Common Vulnerabilities and Exposures and can be any known vulnerability linked to a detected software, there are over 250k CVEs that are known)
Breached or compromised emails
Port checks (open ports, suspicious ports, database exposure, remote access exposure, etc)
Public storage or code repositories
Injection (SQL injection, XSS, etc.)
Broken Authentication and Session Management
Sensitive Data Exposure (personal/SS#, financial/credit card/banking, medical, credentials, company data, etc.)
Security Misconfiguration
Broken Access Control
Cross-Site Scripting (XSS)
Insecure Direct Object References (IDOR)
Broken Authentication
Using Components/Systems with Known Vulnerabilities
Insufficient Logging and Monitoring
Unresolved URLs